- Home
- Knowledge Base
- Managed Services
- Managed Endpoints
- MSx Endpoints Product Description
Solution Summary
The MSx Managed Endpoints service line provides unified performance and security management across a customer’s server and workstation environments. It is designed to keep our clients supported systems healthy, secure, and performing optimally. Support includes remote monitoring and alerting, automated patch management, reporting, and managed next-generation endpoint protection technology to guard against viruses and malware. MSx Managed Endpoints OPTIMUM service also includes comprehensive troubleshooting, support, and system administration. The SECURE Service Level adds advanced security services such as Managed Detection and Response (MDR), DNS Protection, and Security Awareness Training. All services are provided 24x7x365 and delivered by 100% North America-Based support personnel with relevant certifications and experience.
Solution Benefits
MSx Managed Endpoints delivers significant benefits to organizations of all sizes and in all industries. By combining leading support, management, and security technologies, with expert resources available 24x7x365, Our customers can:
Increase Security – MSx Managed Endpoints includes next-generation security software that protects systems from viruses and malware. In addition, our maintenance processes will ensure that security vulnerabilities on systems are patched, which will lessen the chances that an exploit is successful. The SECURE Service Level further enhances our security offering with additional technology and services to actively hunt for and mitigate threats, educate users, and keep systems safe from cyberattacks such as ransomware, phishing attacks, and malicious websites.
Improve System Visibility – MSx Managed Endpoints uses sophisticated Remote Monitoring and Management (RMM) software that constantly collects comprehensive data about the health, performance and security of servers and workstations. This provides technicians and management with valuable information that helps them detect and resolve problems quicker, identify trends that could indicate a larger issue, or facilitate better equipment lifecycle planning.
Shorten Time to Repair – Using the enhanced visibility provided by MSx Managed Endpoints, technicians can be more efficient in their troubleshooting and support efforts. Instead of wasting time trying to identify systems and pertinent information, they can quickly begin troubleshooting. With OPTIMUM or SECURE support, customers also benefit from having a virtual team of TPx technicians that are available 24/7 to address system failures. Shortening the time to repair reduces downtime and lost productivity for our customers.
Enhanced Service Levels – Our team of certified and expert remote resources are consistently trained to keep up with the changing technology landscape. Because we work with hundreds of customers across the country, we have broad experience resolving issues across a wide-range of technologies and use-cases. In addition, TPx manages to a specific service level and we staff to handle peak workloads. All of this allows our team to work very efficiently and effectively to resolve issues, and to deliver a level of service that cannot be matched by most in-house IT staffs or MSPs.
Reduced Support Costs – Many customers struggle with limited budgets, a lack of support technology, and staffing challenges. This often results in poor service delivery and inflated costs because they lack the support tools to help them manage and support systems and users efficiently, or don’t have enough staff to handle the workload, or they over-staff to get the variety of expertise they need. As a leading National MSP, we do not have the same budget constraints that our customers have. We invest in technology and support personnel to meet the needs of our customers and as those needs change and grow we are able to change and grow with them. This allows us to deliver a better and more consistent service level at a reduced cost for our customers.
Maximize Resource Availability – Our certified and experienced MSx Support Personnel become an extension of your staff. By delivering the ongoing proactive and reactive maintenance and administration of our customer’s servers and workstations, your team is freed up to perform other tasks that are more strategic and unique to your business.
Enhanced Investment Protection – Keeping our customer’s systems secure, healthy, and performing optimally will contribute to a longer useful life for that equipment. This protects the customer’s capital investment and it also keeps employees happy and productive, which protects their human investment as well.
Available Service Levels
MSx Managed Endpoints is available in four different service levels to meet a variety of customer use cases.
CORE – The CORE service Level delivers the basic security service that all organizations need. TPx provides Next Generation Antivirus Software (NGAV), as well as patching for windows and select 3rd party applications so the customer’s team can focus on other issues and the customer will know that patching is being done consistently and effectively. We also provide our leading RMM platform and make it available for customer use. Customers can access system status information, take secure remote control, launch available maintenance scripts, and run reports.
OPTIMUM – The OPTIMUM service level includes everything that CORE does and adds remote monitoring, management, troubleshooting and repair by TPx’s experienced support team. All service is delivered by TPx’s U.S.-based support personnel and, should a problem arise, our MSx support team is immediately aware and will begin working to address the issue. With MSx Endpoints OPTIMUM service, end-users can contact MSx support personnel directly 24×7 to request service.
SECURE – The SECURE service level includes everything that OPTIMUM does and adds several high-value security services to significantly reduce customer’s risk and impact of cyberattack. Managed Detection and Response (MDR) provides automatic threat hunting and mitigation with protection that goes well beyond what NGAV can do. DNS Protection delivers advanced security for systems against Internet-based attacks and enhances BYOD and Guest Wifi protection. And finally – Security Awareness Training (SAT) helps ensure that users understand their role and strengthen their ability to keep their organizations safe.
SECURE ENDPOINT BUNDLE – The SECURE ENDPOINT BUNDLE is designed for those companies that will continue to provide their own system patching and administrative support, but want to leverage TPx for the additional high-value security services we offer. This bundle includes NGAV, MDR, SAT and DNS protection.
*Stand-Alone Security Services (Managed Detection and Response, Security Awareness Training, and DNS Protection) can also be contracted individually.
Important Service Considerations
The following information summarizes some key service exclusions and considerations.
Virus remediation: Virus remediation is not included in the standard contract deliverable. Generally, TPx staff will perform initial troubleshooting and routine remediation of viruses using the capabilities included within the TPx-provided Next Generation Antivirus software, or select other tools as a courtesy for OPTIMUM customers. SECURE and SECURE ENDPOINT BUNDLE customers will include automated and advanced mitigation of identified security threats, but we reserve the right to invoice (With prior customer approval) for all virus remediation work.
Hardware Support: requires that the customer maintain a separate hardware support contract. Typically, this is a warranty from the manufacturer, or a 3rd party post-warranty agreement. TPx will manage the ticket from start to finish, assist with troubleshooting, and coordinate with the 3rd party provider who dispatches onsite labor and provides parts. As part of our Life-cycle management service, TPx can offer the 3rd party post-warranty support agreements for an additional charge. Pricing is determined at the time of purchase and based on the equipment manufacturer and model. All TPx support agreements include 24×7 hardware and technical support.
Helpdesk: While the MSx Support team operates like a helpdesk, it is important to qualify this term “helpdesk”, and to ensure that you set customers’ expectations properly. For example, TPx Does not provide “how to” assistance for any applications, or support for Line of Business applications. TPx also does not receive and manage helpdesk tickets for equipment or services outside of the scope of our MSx Endpoints service description.
Application Installation: If during the term of your MSx Endpoints Agreement, you add an additional device or replace a device TPx will provide service as follows:
- For all Servers (All service levels): replacement of server hardware or installation of operating systems and applications is billable.
- For Workstations:
- Standard onboarding of new workstations does not include installation of any software. Software installation will be considered on an individual case basis and may incur additional non-recurring charges.
- Standard support of existing workstations does not include installation of any software. Software installation will be considered on an individual case basis and may incur additional non-recurring charges.
- TPx will reinstall TPx supported software for replacement workstations that are covered under the OPTIMUM or SECURE service levels. Unsupported software installation is available but may incur additional charges.
- Reimaging of workstations is not included in standard service.
*If the customer also has MSx Office 365 service with the appropriate licensing, TPx will install Microsoft Office applications as part of onboarding or support with the OPTIMUM or SECURE service levels.
Application Support: Support for applications falls into three categories; Full support, limited support, and unsupported. A service summary and a list of current applications is as follows:
- Full Support – TPx delivers automated patching, uninstall/reinstall, remote troubleshooting, vendor escalation and ticket management. Applications in this category typically include select Microsoft applications. See the list of full support applications here.
- Limited support – TPx delivers patching and uninstall/reinstall services. Some applications in this category can be automatically and proactively patched using Datto RMM. Other limited support applications can be patched manually on an individual case-by-case basis. You can find a list of limited support applications that identifies which can be setup to automatically patch here. Any additional troubleshooting and support requested for limited support applications may be subject to additional charges.
- Unsupported – TPx does not include support for Unsupported applications as part of the standard monthly recurring service and charges. TPx will consider application support for these on an individual case-by-case basis and any such support may be subject to additional charges.
-
- Customers may request exceptions so that an unsupported application may be treated as a limited support application. TPx reserves the right to deny any requests without explanation. The following minimum requirements should be met by the customer if they wish to be granted an exception:
-
-
- The application should be licensed and/or covered under a valid vendor support contract
- The customer should designate one of their employees as a Subject Matter Expert (SME). This SME will be the focus point for communications between the customer and TPx regarding this application, and will be expected to be involved with the troubleshooting process if a ticket is generated.
-
FULL SUPPORT:
- Microsoft Access
- Microsoft Excel
- Microsoft Outlook
- Microsoft PowerPoint
- Microsoft Teams
- Microsoft Word
- Microsoft Edge
LIMITED SUPPORT: (subject to change without notice)
- Automated patching
-
- 7-Zip
- Adobe AIR
- Adobe Acrobat Reader DC
- Adobe Flash Player
- Adobe Shockwave Player
- Foxit Reader
- Google Chrome
- Java Runtime Environment
- Mozilla Firefox
- VLC Media Player
- Manual patching at customer request
Supported Operating Systems
Microsoft Windows
MSx Endpoints is a Microsoft Windows-based service and while the RMM platform will support a variety of older versions of the operating systems listed below, TPx business policy is to support only Operating System versions that are fully supported by the manufacturer. This is specifically to ensure that security and operational patches are available from the manufacturer. Without these patches, customers would put their businesses at significant additional risk of data loss and downtime due to a cyberattack. Furthermore, TPx would not be able to deliver a consistent and acceptable level of service for our customers without the support of the manufacturer. This policy also applies to Microsoft Office products. The following software versions are currently supported.
Microsoft Windows
- Desktops running Windows 8.1 and 10
- Servers running Windows Server 2012 and newer
- More information from vendor: https://support.microsoft.com/en-us/lifecycle/search
Microsoft Office
- Microsoft Office 2013 and newer, and Office 365 ProPlus
- More information from vendor: https://support.microsoft.com/en-us/lifecycle/search
Other Operating Systems
A limited service scope is possible for VMWare ESXi, Apple MacOS, and Linux systems as identified below. The RMM agent can be installed on these devices and monitoring & alerting is available. Managed patching is not provided, and although several MSx support and MSx Engineering team members do have ESXi and MAC experience, TPx does not specifically hire/staff to support these operating systems. TPx does not have Linux support resources or expertise. Any customer requests for support of VWare, Apple, or Linux systems should be directed to the Product Manager for consideration before committing to quoting any customers.
Service Levels
- For VMWare ESXi: MSx Support Level is Limited Best Effort. ESXi device monitoring available.
- For macOS: MSx Support Level is Limited Best Effort. macOS device monitoring is available.
- For Linux: MSx Support Level is None. Linux device monitoring is available
Operating Systems
- VMware ESXI
- Remote monitoring agents installable on OS X 10.7+, but tested on latest two versions of the operating system
- Fedora, Debian, CentOS (requires yum-utils), and Ubuntu: latest two versions
- RedHat Enterprise Linux 7 and later using EPEL
- Mono, .NET compatibility software, will be installed on Linux-based systems
Service Details
Remote Monitoring and Management
MSx Endpoints leverages Datto RMM Remote Monitoring and Management (RMM) Software. Using DATTO RMM, MSx support technicians can collect information about the health and performance of a customer’s endpoint hardware and software, monitor and alert on endpoint issues, deploy patches, and schedule maintenance jobs. This cloud-hosted technology platform, combined with our best-practice configuration, allows TPx to deliver powerful automation and support capabilities that create a robust set of IT services that drives operational efficiencies, increases system security, and ensures we can provide extremely reliable service levels. The MSx Endpoints platform allows us to manage end users and clients while achieving the most efficient use of IT resources possible and offers the broadest and deepest set of IT management capabilities in a single solution.
The Datto RMM platform consists of two separate applications: the RMM Portal and the RMM Agent. The RMM Portal is a cloud-based browser application that is used by TPx technicians to securely and remotely manage devices across all our clients. The RMM Agent is a lightweight software program that is installed on all supported devices. It collects data on the devices and communicates it to the Portal.
Note: RMM features and services are available based on MSx Endpoints service levels. Refer to Available Service Levels for details.
RMM Portal Overview
The RMM Portal is the endpoint management control console. It is cloud-based and delivers exceptional availability and scalability. The Platform is built using a secure multi-tenant architecture that allows different levels of access and roles so that TPx can efficiently manage all our customers, while allowing our customers own IT staff to securely access and manage their own systems. To further enhance security, Multi-factor Authentication is required to login to the RMM platform as an Administrator. When logged in as an Administrator all the functionality That TPx Technicians and authorized Customer IT Staff need to manage their endpoints is available from a single pain of glass. The user interface is very intuitive and easy to navigate, allowing easy drill down from Site to groups to individual machines. Additional information on the Datto RMM Platform Architecture and Security can be found here.
Many of the RMM Portal functions and settings are configured at the Global level and are used / accessed only by TPx technicians. This includes, for example; setting up patching and monitoring policies and standard reporting. Customers can, however, leverage the RMM Portal to self-manage their own supported endpoints using components which include application installers, third-party integrations, scripts, or even device monitors. Customers can also contact TPx Support to request a new component be made available for them. Billing for such requests will be considered on an Individual Case Basis (ICB). The list of components that TPx makes available to its clients is currently over 70 and more are added frequently. Components are grouped into the following categories.
- Applications – The Applications category contains programs such as web browsers and browser plug-ins, Adobe products, Flash players etc., ready to be pushed out to as many endpoints as required.
- Integrations – Integrations enable Datto RMM to connect to PSA platforms, such as Autotask PSA.
- Device Monitors – Device monitors allow you to monitor the state of your devices, e.g. backup, services, processes, antivirus, and more.
- Extensions – Extensions provide additional functionality, such as Mobile Device Management or Splashtop Remote Screen Sharing.
- Scripts – This area contains scripts for activities, such as installing uVNC mirror drivers, clearing the print spooler, rebooting the system, and various other useful tools.
RMM Agent Overview
The MSx Endpoints platform manages machines by installing a software client called an “Agent” on a managed machine. The Agent is a system service that does not require the end user to be logged on for the agent to function and does not require a reboot for the agent to be installed. The agent software also has a very small footprint and communication uses extremely low bandwidth so these items should not impact system or network performance.
The agent communicates securely with the cloud RMM Portal to provide specific information about device health, properties, and performance. It can execute a variety of actions on the remote device such as:
- Audit the installed hardware and software
- Proactively monitor the device
- Deploy software, patches, and updates
- Enable the remote takeover of devices that have the Agent installed
The Agent allows IT staff to manage remote devices through the Agent Browser, which is an application launched from the Agent. Through the Agent Browser, TPx technicians, or authorized Customer IT staff can perform many remote support tasks. It allows you to diagnose and fix many issues remotely, and often in the background, without the user being aware of it. Some of the tasks you can execute through the Agent Browser include:
- Take a screenshot of the remote device or open a remote takeover tool like RDP, VNC, or Splashtop
- Open a Command Shell and add and edit registry items on the remote device
- Control Windows Services on the remote device
- Wake up, shut down, or restart the remote device
- Monitor resources such as CPU or memory in real time
- Manage files
- View event logs
- View drive information
- Deploy the Datto RMM Agent to devices on the remote network
See here For a list and explanation of the Agent Browser tools available for Windows devices.
When the agent is installed on an end-users Endpoint, the end-user will see a small MSx icon in their system tray. By right clicking this they can launch the Self-help Portal which provides the following capabilities:
- Summary: Summarizes device information such as hostname, IP Address, Manufacturer, Model, Serial Number and key specifications
- Tasks: This page provides some self-help resources where users can run certain fixes on their own. (Such as a disk cleanup)
- Tickets: End-users can submit support requests directly from the agent portal.
Device Auditing
An audit is an inventory of the hardware and software installed on a device as logged by the Datto RMM Agent. Auditing provides valuable information that is used in both troubleshooting and planning. If a technician is troubleshooting an issue on a PC, they can, for example, immediately determine the current patch level, check CPU performance, and verify Windows Process status to gain an immediate understanding of the PC’s current status. If management is planning to upgrade to a new software application which requires that PCs and servers meet certain minimum requirements (CPU speed, Memory, Disk Space, Operating System version, etc) and needs to determine if existing systems will support the application, they can quickly access this information for individual devices or in mass.
As consecutive audits are performed, changes to the hardware and software are tracked in a change log. The data is stored on the device and added to the device record in the RMM Portal. Network discovery information is also displayed on the Audit tab. The following audit levels are available:
- Account: View all sites’ discovered devices in a table form. You can also see all hardware and software installed on the devices associated with all sites in the account, including quantity and version information.
- Site: View the discovered devices in the site. You can also see all hardware and software installed on the devices associated with that particular site, including quantity and version information.
Monitor the number of devices a software package is installed on. This allows you to manage site or team licenses. - Device: View all hardware and software currently installed on that particular device. You can also see the status of the installed Windows services and the changes that have been made to the device over time.
- Account and site: Monitor the number of devices a software package is installed on. This allows you to manage site or team licenses.
There are two types of audits performed in Datto RMM. A full audit is a complete inventory audit of a device taken at the time the Agent is installed. A full audit of a device can also be initiated manually at any time. A delta audit is a list of the changes to the audit information on the device since the last audit. Delta audits are performed automatically every 24 hours. Delta audits are also performed after successful completion of a job, after patches have been applied, or can be performed manually at any time.
Details about the Audit Information available within the RMM Portal can be found here.
Monitoring and Alerting
Using the RMM Platform, TPx delivers 24x7x365 device monitoring and alerting. Since CORE customers are responsible to self-administer their devices, these customers will directly receive the alerts, allowing them to quickly identify and address problems. OPTIMUM and SECURE customers receive comprehensive maintenance and administration by TPx’s certified and experienced technicians. Alerts for OPTIMUM and SECURE customers are received and addressed directly by TPx 24x7x365. SECURE ENDPOINT BUNDLE customers do not receive monitoring and alerting through the RMM platform.
Monitors keep track of a variety of attributes, processes, settings, statuses, events, and much more, on devices they are deployed to, and raise an alert when the device is not operating within specified parameters. Datto RMM provides a comprehensive list of monitor types and categories.
TPx configures our monitoring policies based on the device type, operating system, and role. A Windows File Server will have different monitoring and alerting requirements than a Windows SQL Server for example. Multiple Policies can be applied to individual machines, which allows TPx to provide comprehensive alerting profiles for a wide-range of hardware and operating system errors, events, and statuses. When a specific trigger is set – such as a stopped windows process or a spike in CPU or Memory usage, the system automatically alerts. This allows TPx Technicians to quickly identify an issue and proactively begin troubleshooting & repair.
The list below shows various devices for which we have configured Standard Monitoring Policies. See details about these Standard Monitoring Policies here.
- Windows: Hardware Events
- Windows: Server
- Windows: Workstation
- Windows: Role – DHCP Server
- Windows: Role – DNS Server
- Windows: Role – Domain Controller
- Windows: Role – Exchange Server
- Windows: Role – Hyper-V Server
- Windows: Role – IIS Webserver
- Windows: Role – SQL Server
- Physical Servers
- Servers – Dell
- Hardware: DELL Server Event Logs
- Servers – HP
- Hardware: HP Server Windows Event Logs
- Hardware: HP Server ILO (Array)
- ESXi Monitor Policy
- APC Windows Event Log Monitor
- Operating System: macOS
- Datto RMM Agent
Remote System Support
Remote system support is included with the OPTIMUM and SECURE service levels. With the CORE service level the customer has access to perform remote system support using the RMM Agent, or they can request billable assistance from TPx technicians. Service is delivered 24x7x365 and includes proactive maintenance, system administration, and troubleshooting & support of issues as a result of an alert of customer request. Examples of support tasks include, but are not limited to:
- Accessing system audit information to determine device HW & SW inventory
- Reviewing system logs, disk space, CPU and memory utilization, and other KPI’s to quickly identify system health and status.
- Performing specific updates to fix software or hardware issues
- Running system maintenance scripts to resolve identified issues
- Performing antivirus scans
- Accessing the end user system via remote control to actively troubleshoot and resolve systems problems.
- Opening and managing support tickets with 3rd party hardware manufacturers or pre-approved SW vendors.
- Proactive notification of pending warranty expiration for supported servers
The RMM Agent delivers real-time remote control across distributed networks so a technician can perform maintenance tasks from any location without ever disturbing the end user. If a User is requesting support, the Technician can also take remote control of the users’ session and directly assist the user. To enhance security, Remote Control is configured to be accepted by the end-user. To take remote control of a device, the technician clicks a button to request it and the user then sees a prompt to accept or deny the request. End-users can contact TPx for assistance but only the designated Customer Point(s) of Contact can authorize service that is outside the scope of standard monthly charges.
Patch Management
System Patching
A patch is an update to a computer program or system to improve performance or fix existing flaws such as security vulnerabilities, bugs, or other issues. System patching is necessary for all businesses, period. Windows systems are especially vulnerable to cyberattack, and system performance and reliability can be significantly impacted if systems are not properly patched. It is, therefore, important to ensure that patching is completed regularly and consistently. But, It can be difficult to know which patches should be applied. System patches can negatively impact performance for any number of reasons – maybe the hardware is too old and doesn’t have enough resources to handle the new patch, or there are hidden issues within the patch itself that affect system operation. It can be a time-consuming and frustrating task for a business to manage the process of patching their systems internally. System patching is included in MSx Endpoints CORE, OPTIMUM and SECURE service levels. Our service ensures that the right patches are applied on a timely and consistent schedule, freeing our customer’s internal IT staff from the burden of managing this important process.
TPx provides managed patching of select Microsoft Server and Workstation Operating Systems and Software, as well as approved 3rd party applications. Once approved, the individual agent configuration will govern the automated deployment of all missing approved patches based on a mutually agreed upon schedule and reboot selection. Generally, workstations are patched daily from 10am to 12pm EST. Servers are patched the 3rd or 4th Wednesday of each month and scheduled off-hours. Urgent security patches may be applied immediately based on individual circumstances.
Patching Policy for Microsoft Windows
Critical Updates, Security Updates, Applications updates, Definition Updates and general Updates are auto-approved within 14 days of release unless TPx pushes a zero-day patch or holds back a patch that has been identified by the news and personal experience to adversely affect the end user experience.
Service Packs, Feature Updates (akin to Windows 10 service packs), Cumulative Updates (which often include blacklisted patches and nagware) are not automatically pushed, but should be scheduled and rolled out gradually due to size and likelihood of impacting user performance.
Drivers and BIOS/EFI are not updated except to resolve an issue known to be corrected by an update.
Patching Policy for 3rd Party Software
Approved third party applications are updated if installed, as the respective vendors release updates, and when Datto adds the installation packages to their repository. Individual applications, such as Java, may have updates disabled, if updating the utility may have adverse effects to a Line-of-Business application.
Currently the automatically patched list is: 7-Zip, Adobe Air, Adobe Acrobat Reader DC, Adobe Flash Player, Adobe Shockwave Player, Foxit Reader, Google Chrome, Java Runtime Environment, Mozilla Firefox, VLC Media Player. Also available but not activated: FileZilla FTP Client, Notepad++, Paint.NET, PuTTY, Skype. Datto is continually adding to their list.
Any application available from Ninite Pro can be managed separately from the native Datto RMM Software Management module, upon request.
Other 3rd-party applications may be deployed by the RMM platform if the package can be run silently at the system console level. Development and testing of a custom script can be requested by a customer as a separate service ticket. This work may be billable.
Consistency and Compliance Audits
The audit and assessment elements of this patch management program are in place to help identify systems that are out of compliance within an organization. Where systems and security are in a constantly evolving state, patch management is an ongoing set of processes designed to ensure the most secure and stable environment possible, without preventing users from performing their primary duties with undue interruptions. To supplement post-implementation auditing, patch audit scans have been scheduled to track and maintain the patch level database for all systems covered under patch management.
A full audit scan occurs on agent installation. Delta audits occur every 24 hours, as well as upon completion of any scheduled job, or completion of a patch cycle. This ensures that the latest audit data is available for review in the event a critical mid-stream patch is detected as being needed for any server or workstation. Full and delta audits may be scheduled on an “as needed” basis in the event it is required for regulatory or third-party compliance audits.
Newly rebuilt or deployed systems that are introduced into this patch management program will be added to the existing patch schedule and reboot configuration for the respective site to which they are being installed, unless an override is otherwise specified by the build or agent deployment request. Outstanding patches will begin deploying automatically during the next scheduled patch cycle, which may adversely affect the end user experience.
Monthly consistency and compliance reviews are performed prior to the approval of all newly released updates to identify errors or failures that are preventing systems from attaining compliance with the patch policy that is assigned to the agent. Remediation is performed on an as needed basis across all client systems.
TPx can make no guarantee of patch compliance for systems that are not online and available on a regular basis.
Approval Process
TPx provides a 3-phase approach for the review and approval of regularly scheduled update releases. Each phase is intended to ensure the timely and safe deployment of newly released updates.
Research Phase
TPx will research and assess the effect of newly released updates to the Client prior to its deployment by analyzing the criticality, scope, and potential impact on security, regulatory and industry compliance requirements.
If TPx categorizes a patch as an Emergency, the Patch Management Team considers it an imminent threat to the security of our client’s networks and assumes the greater risk is not implementing the patch vs. not waiting to test it before implementation.
The Research Phase is typically completed within 2 business days after a regularly scheduled patch release date, but may be extended for any update found to have significant negative or undesirable side effects.
Review & Testing Phase
Updates deemed Normal or Non-Critical will undergo standard internal testing for each affected platform before general approval is made. TPx will expedite testing for critical patches in a manner dictated by the criticality of the update. The Patch Management Team will complete validation against all available operating systems prior to approval.
The Review & Testing Phase is typically completed within 3 business days after a regularly scheduled patch release date, but may be extended for any update that is found to have significant stability issues or a high incident of installation failure. Updates that fail the testing phase will be returned to the Research Phase until a suitable workaround can be found, a new version of the update is released by the vendor, or the security concerns addressed by the update outweigh the risk of introducing a potentially unstable update into a client’s environment.
Approval Phase
Updates that have reached the Approval Phase have been certified through research and testing to be warranted, stable, and ready for deployment within the standard TPx Patch Management offering. Production deployment is typically authorized no more than 3 business days after regularly scheduled update release dates.
A note on Windows 10
TPx is unable to withhold patches indefinitely on Windows 10 operating systems. With Windows 10 Pro, Enterprise, Education and S systems, Microsoft permits us to defer feature (service pack type) updates a maximum of 365 days, quality (security) updates a maximum of 30 days; by which time broken patches should be rectified. Windows Home edition will not permit any delay of operating system updates.
Ongoing Analysis
Updates that are approved and are found to have compatibility or stability issues, or induce adverse effects on the performance of third-party and line of business applications not included in the Review & Testing Phase, will be returned to the Research Phase for escalation to a product specialist or vendor support for remediation. Updates already deployed that meet these criteria and that permit removal will be uninstalled by script from any system found to contain the update. Updates that do not permit removal after installation may require special scripting to manually remove the update.
Ongoing analysis has no set expectation of action unless an issue is detected and reproducible. Standard Escalation SLAs apply.
Default Reboot Policy
New clients will be assigned our default patch and reboot policy, to ensure that operating systems and applications are kept up-to-date and secured as much as possible against new exploits, with as minimal user impact as possible.
Workstation Policy
- Frequency: Every weekday
- Patch window: 10am to 2pm at local time zone of the agent software
- Local Cache: Use a Local Cache to download and distribute updates to targeted devices if available; used for larger enterprises; not available in Windows 10
- Reboot action: Do not reboot devices after patch window has concluded but show Endpoint a branded reboot reminder every 24 hours until rebooted
- Expectation: Customer is expected to reboot/shutdown their machine every night for the updates installed during the day to be applied
- 3rd Party Software Patching: Deploy 3rd Party utility software application updates listed in the Products Managed section above, immediately upon availability to the RMM platform
Server Policy
- Frequency: Monthly on 3rd Thursday
- Patch window: 9 pm to 10 pm at local time zone of the agent software (patches starting late in the hour may extend into and complete in a second hour)
- Local Cache: Use a Local Cache to download and distribute updates to targeted devices if available; used for larger enterprises; not available in Windows Server 2016+
- Reboot action: Reboot automatically once patching concludes, unless the server is a Hyper-V host or the policy is overridden at the site or device level
- 3rd Party Software Patching: Manually upon request, dependent on role; if terminal server, we’ll deploy standard 3rd Party utility software application updates listed in the Products Managed section above during a arranged maintenance window
The client may choose options from both of the Scheduling Options and Reboot Action sections below, if the default policy proves undesirable or user impacting. Adjustments after onboarding must be submitted via ticket or request, from a contact authorized to make changes to the customer account, and in the format “[Device Name or Type], [Day Choice] at [Time Choice], and [Reboot or not]”.
Warning: Patch Management for mobile systems frequently connected to cellular networks should be restricted to predefined times when the user will be connected to standard Wi-Fi or wired networks, by having the machine placed in a separate site with its own Patch Policy or no Patch Policy.
Scheduling Options
Run Once / Manual Scheduling
Primarily used in the On-Boarding phase of an agreement to bring endpoints into compliance with current approval policies and patch levels. This scheduling option is not intended for regular use and may incur labor charges with excessive use.
Daily
Primarily used for workstation, laptop and mobile devices. This scheduling option is frequently coupled with the “Do not reboot” option to permit timely deployment of updates while minimizing the interruption of an end user’s productive hours. (Example: Patch every day at 6am)
Weekly
Primarily used for static workstations and load balancing purposes in larger organizations. This option allows for the selection of one or more days of the week to apply updates, and can be coupled with any of the reboot options listed below. (Example: Patch every Tuesday and Thursday at 8pm)
Monthly or Quarterly
Primarily used for servers requiring a less frequent deployment cycle. This option permits the deployment of updates with the [First | Second | Third | Forth | Last] and [Day | Sunday | Monday | Tuesday | Wednesday | Thursday | Friday | Saturday | Sunday | Weekday | Weekend Day]. (Example: Patch every month on the 3rd Tuesday)
Yearly
Not recommended for use except in very specific circumstances. Select the day number of the year [1-365] to be run on that day annually.
Reboot Action
Reboot immediately after update.
If necessary, it will reboot the targeted devices after the policy has run.
Do not reboot after update.
It will stop the targeted devices from rebooting after the patch schedule window.
- Show Endpoint a reboot reminder every X hour/day; every 1-12 hours/1 day/2 days
- The reminder will be displayed on the screen until the end user dismisses it
- The reminder can be dismissed indefinitely
- Permit a maximum of X dismissals, after which time reminders will persist on screen
Next Generation Antivirus (NGAV)
MSx Endpoints includes an integrated Next Generation Anti-Virus and anti-malware software (NGAV) for enterprise class endpoint protection designed to help further secure customer endpoints from viruses, malware and other threats.
NGAV Software Overview
MSx will always look to leverage the best and most reliable Next-Gen AV available, currently leveraging Webroot’s SecureAnywhere Endpoint Protection. Webroot SecureAnywhere is integrated with and managed through the MSx Endpoints RMM platform. The software can be deployed automatically to an endpoint through the RMM agent. Once deployed, it provides continuous security for that Endpoint. It also reports back it’s status and alerts to the RMM platform to enhance live support and reporting capabilities. Some important characteristics of Webroot SecureAnywhere are:
- Its ultra small agent is less than 1MB, takes under 5* seconds to install, and requires only 2MB* of hard disk space, while the typical
antivirus averages over 1GB - As a fully cloud-based solution, malware definitions are in the cloud, not downloaded onto the endpoint, so it’s always up to date
- Lightning-fast scans use only 10%* of CPU and take around 91*seconds, so they never interfere or slow users’ devices down
- The agent doesn’t conflict with existing antivirus
- The day to day operational costs of our Next Gen AV are less than those of a traditional antivirus – even if it’s free
Some of the unique benefits of Webroot’s smart Endpoint Protection are:
Detection
- Behavior-based, not signature-based allowing it to address a wider array of attacks, including Zero-Hour attacks.
- One of its kind, cloud-based, adaptive protection
Management
- Customer satisfaction rating of over 94%
- Tiny <1 MB agent designed for minimal footprint
- No signature updates
- Minimal user performance impact
- All endpoints protected collectively & managed centrally
Collective Protection
- Any time a Webroot-protected device encounters a threat, all other endpoints are secured in real time
- Data from tens of millions of sensors is correlated and analyzed continuously
- Machine-learning backs highly accurate real-time analysis of URLs, IPs, files, mobile apps, and phishing sites
Remediation
- Software’s rollback remediation automatically undoes changes made by malware
- No need to re-image or wipe devices
NGAV Management Services
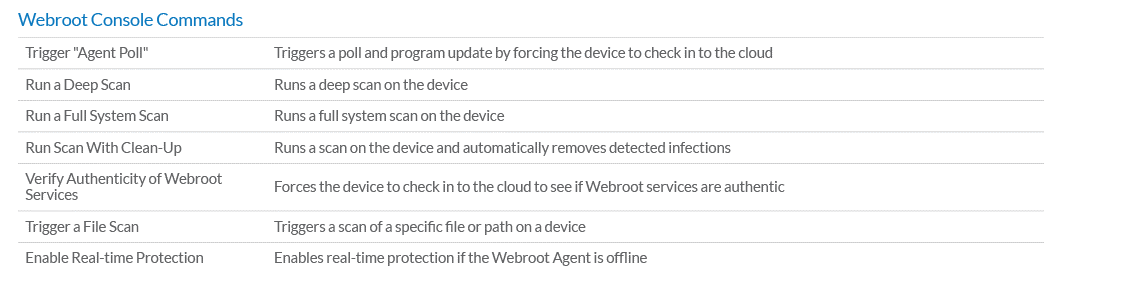
TPx technicians monitor and support Webroot directly through the Datto RMM Platform. During MSx Endpoints onboarding, TPx creates a Security Management Policy which allows us to push out the Webroot software to all supported endpoints and generate alerts and tickets as per the criteria set in our standard monitor policy. Using the Datto RMM Platform, TPx technicians can install or uninstall Webroot and can include or exclude selected devices from a site’s Security Management Policy. Technicians can also execute the following Webroot Console Commands right from the Datto RMM Platform.
Reporting
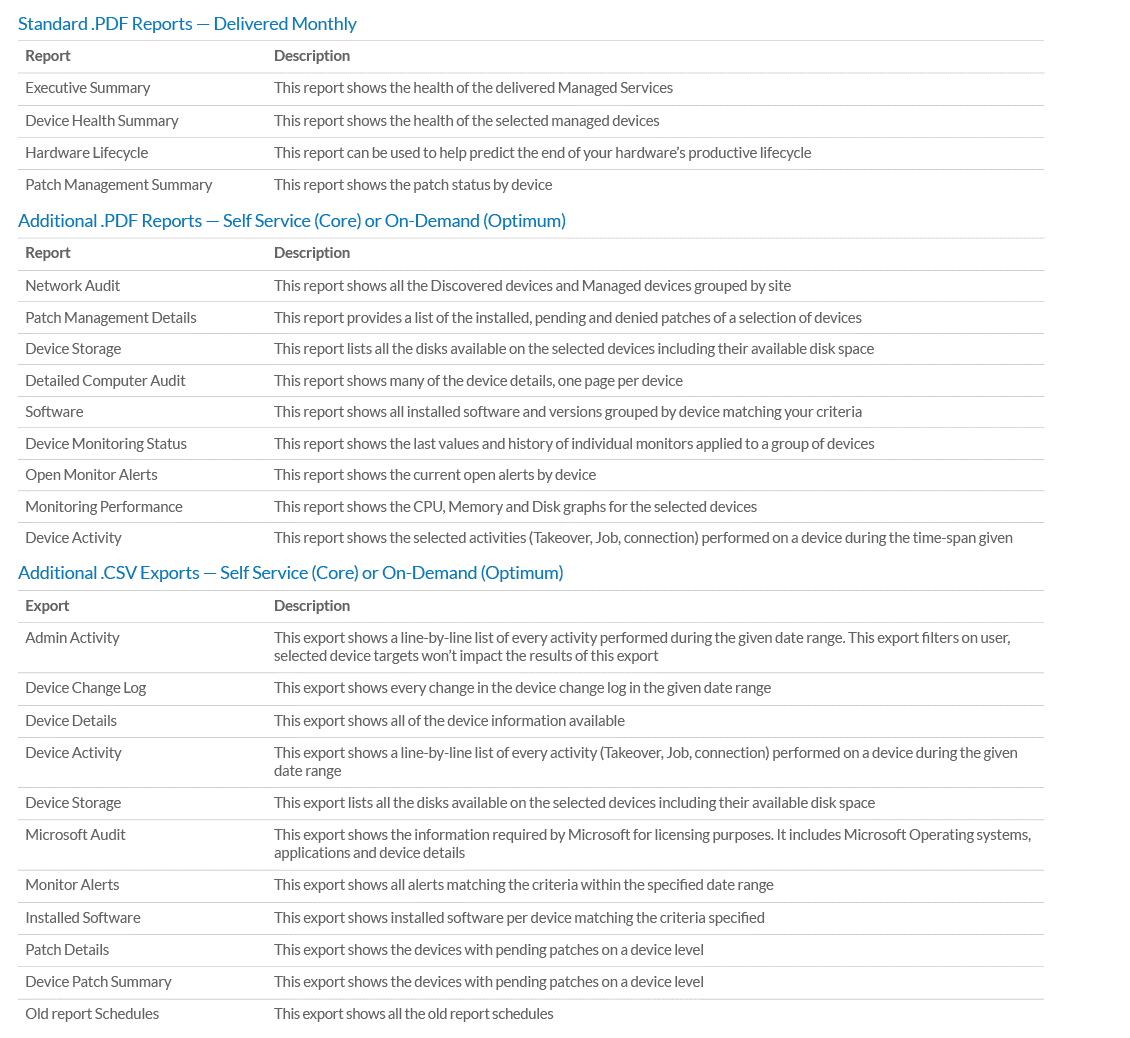
Webroot reporting is integrated into the standard RMM reports. The following reports include Webroot information.
- Executive Summary Report: Summarizes the QTY of devices with Webroot installed and overall status (Up to date, running…)
- Device Health Summary: Indicates, per device, which devices have Webroot reporting as updated and running and which are reporting an issue
- Detailed Computer Audit: Indicates, per device, all SW installed on the device
- Software: Indicates how many devices have a particular SW version loaded on them
- Installed Software Export: .csv export showing what devices have particular software installed on them
Managed Detection and Response
Managed detection and Response (MDR) combines advanced Endpoint Detection and Response (EDR) technology with proactive security monitoring, threat hunting, and mitigation to prevent security breaches before they happen and minimize the potential damage caused by a security breach.
MDR Overview
TPx leverages best-in-class Endpoint Detection and Response Technology (EDR) from GoSecure. This technology delivers superior threat detection than competitive solutions. It detects malware on-disk and suspicious behavior in the OS, and is the only solution that detects advanced threats in physical memory. Using its patented Digital DNA (DDNA) technology and advanced machine learning the GoSecure EDR platform detects, prioritizes, and mitigates threats faster and more efficiently than competitive solutions. Combining this best-in-class software with experienced Security Analysts, that monitor our customers’ environments 24x7x365 and perform advanced threat hunting and incident response, allows TPx to deliver a truly superior Managed Detection and Response service to our customers.
Automated Threat Detection
Next Generation Antivirus (NGAV) protection, while a necessary and very important piece of the puzzle, is not enough to deliver proper protection anymore. Today’s security landscape sees Cyberattacks growing exponentially and increasing in complexity. Next Gen AV will never be able to keep up and provide 100% efficacy. Our predictive Endpoint Detection and Response (EDR) software helps deliver on what NGAV cannot, by providing a more comprehensive approach to threat detection. For example, a new zero-day attack may be able to successfully evade NGAV detection, but EDR can prevent it by identifying and correlating different processes and behaviors happening on systems or the network that are indicators of Compromise. Some of these include:
- Suspicious Execution:Often, legitimate processes, can be highjacked by cybercriminals. For example, running a Powershell Script on a device may normally be a perfectly legitimate event, one that raises no alarms in your antivirus program. Our EDR software can detect a compromised Powershell script that has malicious intent when executed, and block it.
- Lateral Movement:Malicious actors often gain access and move between devices and applications inside of a network to attain higher levels of privileges, credentials, or access. NGAV solutions do not detect this behavior as malicious whereas our EDR software will recognize such behavior, block it, and alert our Security Analysists who can perform additional advanced threat hunting and mitigation.
- Privilege Escalation:By exploiting a vulnerability inside of an operating system, software application, or hardware implementation (a bug, design flaw, misconfiguration, outdated software version, etc.), a malicious actor can gain elevated access to network or device resources. Gaining such elevated access is not something that is identified as a problem by most endpoint security software, but it can enable the attacker to take specific action to further compromise an environment. Our EDR software and Threat Detection services can identify these issues to further enhance protection of your environment.
- Persistence:Persistence refers to the use of tactics, techniques, and protocols to decrease the likelihood of removal of a malicious actor from an infected or compromised network over an extended period. These techniques are used to conduct “Advanced Persistent Threats (APT)” which gives an attacker time to gather more information, identify and exploit other vulnerabilities, and steal data over a prolonged period. Quickly identifying APTs reduces dwell time and is an important benefit of our service.
- System Control:System control is the use of tactics, techniques, and protocols by a malicious actor to gain access to the entire information system (server, workstation, network device, etc.). This type of complete system control is often the most dangerous type of attack and can allow attackers to steal data, spread malware, disrupt web services and more.
The advanced capabilities built into our EDR software allow it to identify these Indicators of Compromise, detecting threats that utilize multiple attack vectors and are hidden by leveraging otherwise legitimate system actions to accomplish their attacks. Threats are quickly analyzed and detected, typically in under a second, minimizing their ability to execute or cause damage.
Automated Threat Mitigation
If a threat is found, the system can instantly take automated action to mitigate it. Examples include quarantining compromised systems, killing processes, and deleting malicious files. These automated mitigation actions can eliminate many threats on their own, reducing costs, minimizing damage, and allowing security personnel to focus on high priority threats and those that require additional threat hunting and advanced mitigation activity.
Customized Detection and Mitigation Profiles
Cutting through the ‘noise’ (eliminating false positives and false negatives) is an important part of any MDR solution. At TPx, we start with GoSecure’s best-in-class EDR software and our team of experts customizes it to the unique requirements of each customer. By doing so we can maximize efficacy and efficiency, and eliminate the noise that many other MDR solutions produce. This allows our Security experts to focus their advanced threat hunting and mitigation efforts on the events that really matter to deliver faster, more efficient, and reliable results.
Advanced Threat Hunting & Mitigation Services
Many advanced threats cannot be eliminated using software alone. They require additional threat hunting and mitigation from expert security resources. TPx’s MDR solution includes a team of specialized security analysts that are available 24x7x365 to perform these advance threat hunting and mitigation services. This service includes an industry leading 15 minute detection-to-mitigation response time. Individual incident reports are emailed after each event so customers can understand what happened, what system(s) were compromised, what action was taken, and what additional recovery steps are recommended. Scheduled monthly reports are also delivered.
Threat Prioritization
Threats identified by the EDR software can range in severity. As such, it is very important to ensure that security personnel can easily identify the most damaging threats and focus their attention on eliminating them. Doing so further enhances the cost-efficiency, reliability, and speed of our service. TPx Managed Detection and Response service groups threats by severity within the monitoring dashboard. Groupings and examples include:
- Urgent ( 15 Minute Response Time)
- Compromised Endpoint. No EDR Mitigation
- CNC Activation, Ransomware, Malware
- High ( 30 minute Response Time)
- Compromised Endpoint with EDR Mitigation
- Communication with a Malicious Site, Including Exploit Attempts
- Malicious File Found on Endpoint
- Malicious Email Found
- Medium ( 1 Hr Response Time)
- Communication with Phishing site. Credential Compromise Unconfirmed
- Exploit Attempts (Excluding Exploit Kits) What/Why?
- Policy Violation (Use of TOR, Unauthorize Proxy Services)
- Low ( *See note below)
- Potentially Unwanted Programs/Adware
- Credentials Visible in Plain Text
- Policy Violations: Out of Policy Behavior, Gaming, Downloads, P2P Activity
*Low priority alerts are suppressed as per GoSecure best practice because the vast majority of customers do not want to get these alerts. Instead a weekly report detailing low level events is provided via email. A section of the monthly customer report will also summarize the low level alerts and recommended action. Customers can choose to turn on reporting of low level events if desired by opening a support request with TPx.
Reporting
Each month, customers will receive a comprehensive report that provides the following information:
- Count of covered endpoints
- The number of events analyzed for Evidence of Compromise during the month
- Observed threat alerts in the last month, broken out by type of threat
- Observed threat alerts in the last month, broken out by priority
- 12 month rolling summary of the observed threats investigated and escalated to customers
- 12 month rolling summary of escalations broken down by category
In addition a weekly report detailing low Level Events will be sent separately.
The report will be sent, via email, to the designated authorized contact at he customer.
Security Awareness Training
Considering that 90% of successful breaches were caused by user error, it’s no surprise that the right Security Awareness Training program can greatly enhance any businesses security. By implementing regular Security Awareness Training that includes phishing simulations and teaches employees about cybersecurity, IT best practices, and regulatory compliance businesses can experience fewer breaches and significantly reduce risk, decrease instances of infection, reduce IT costs and protect their reputation. TPx’s Security Awareness Training includes monthly phishing simulations and online training courses. Learners are enrolled in the training program and then phishing simulation emails and training courses are delivered automatically. Automated program management and reporting is provided to help customers achieve success and track progress toward their security awareness goals. The TPx Security Awareness Training Program follows the NIST cybersecurity training guidelines to help you achieve NIST compliance.
All training content is owned and provided by The Infosec Institute. The Infosec Institute InfoSecIQ learning platform is a Gartner Magic Quadrant Leader in Computer-based Security Awareness Training.
Phishing Simulations
Go To: Page Menu > Service Details Menu > Awareness Training > Reporting
To execute phishing attacks, criminals send emails impersonating your organizations internal IT department or well-known companies such as Microsoft, Google, Amazon, Paypal, Bank of America, etc. These emails try to get users to click specific links, which are malicious in nature and can cause serious data loss or system downtime. The Security Awareness Training service from TPx includes automated monthly anti-phishing campaigns to educate users which, over time can reduce phishing email click rates by 75%. Each month, three different phishing email will be sent to the customer’s enrolled learners. Emails will be sent, randomly over the course of the month, using pre-built templates that mimic real-world phishing attacks. Any user that “takes the bait” by clicking on a link is directed to additional training materials to help them understand how to better recognize phishing emails and prevent clicks in the future. A separate “You’ve been phished” email is also sent, letting them know that they were phished as part of the company’s Security Awareness Training program and inviting them to review the training materials again.
Awareness Training
In addition to the monthly Anti-phishing campaigns, TPx will deliver automated Security Awareness Training courses to customers. These courses consist of a range of topics from general security awareness to best practices and regulatory compliance. Our Security Awareness Training program follows the NIST guidelines outlined in NIST Special Publication 800-50, which recommends that security awareness and training cover the following nine topics:
- Phishing
- Password security
- Safe web browsing
- Social engineering
- Malware
- Mobile security
- Physical security
- Removable media
- Working remotely
remaining monthly training courses (Months 10-12) will be assigned based on customer specific needs to strengthen regulatory compliance or to enforce company policy. Customers will choose 3 of the following course topics
- HIPAA
- PCI
- NIST
- GDPR
- FAR & DFAR
- GLBA
- CJIS
- Advanced awareness topics
- Awareness refresher course
Each month, Learners will receive an email welcoming them to take the training course with a link directing them to the Course Page. Reminders will be sent to Learners to encourage them to complete the course to improve adoption rates.
The Course Page gives your employees the flexibility to complete training in their preferred language. After training is assigned, each employee can self-select their language before completing a module or take training in the default language you assign.
Learners will also have access to a DASHBOARD which allows employees to continue in-progress training assignments and revisit completed courses and training modules.
Course content will be modified and updated as needed based on changes in industry regulations, security best practices, NIST guidelines, etc.
Security Awareness Posters: Keeping employees informed about the importance of maintaining proper security habits is a key element in any Security Awareness Training Program. For this reason, we give our clients an easy way to keep security front of mind when users are away from their computers. Customers who enroll in this service will receive a series of Security Awareness Posters in .pdf format which they can print out and display around the office.
TPx support is available 24x7x365 to answer questions about the program, provide technical support, and add/remove Learners from active enrollment.
Reporting
TPx’s will provide automated weekly reporting for customers. Reports include:
- Phishing Campaign Summary: Summary statistics on the active phishing campaign (# of Learners enrolled, % Phished, % Entering Data, % Opening file)
- Awareness Campaign Summary: Summary statistics on the active learning campaign (# of Learners enrolled, % started, % completed)
- Active Learners List: List of active employees enrolled in the program
DNS Protection
Domain Name System (DNS) Protection protects endpoints against compromise from malicious websites and Internet threats by redirecting user web traffic through a cloud-based, DNS security solution. DNS protection helps enforce web policies, ensure regulatory compliance and can stop up to 88% of threats at the network edge before they ever hit the network or endpoints. Content Filtering for off-network devices also delivers extra security for systems that are using home networks, 3rd party networks, or public wifi hotspots.
TPx DNS Protection service is powered by Webroot’s world-class Threat Intelligence which is trusted by over 90 network and security technology vendors worldwide to enhance their own solutions. Webroot scans the entire Internet at least 3 times per day, continuously correlating and contextualizing global threat data in real and near-real time. DNS Protection is delivered by redirecting users web traffic to Webroot’s DNS Servers, which will then identify and block requests destined for dangerous or questionable sites such as malware or adult, or unwanted sites, such as streaming media. Over 80 site categories allow for granular, policy-based control.
Windows devices can be deployed using a DNS Protection agent that allows them to receive protection both from within, and while outside the corporate network. Other devices such as guest wireless users, mobile devices, and any other non-windows devices that need to make Internet DNS requests from within the corporate network are protected by the Network-based DNS protection.
Endpoint DNS Protection
The primary method of DNS Protection deployed with MSx Endpoints is Endpoint DNS Protection. This is available for Windows devices and leverages the Webroot SecureAnywhere NGAV client that is already deployed to these devices as part of the MSx Endpoints service. Deployment using the SecureAnywhere agent eliminates the need for a separate DNS agent and keeps devices protected while users work from coffee shops, airports or other locations on the go. It also protects systems while connected to the corporate network. While on the network, or connected via VPN, any Internet DNS requests made by a protected system will bypass the client’s existing network DNS servers and be routed through Webroot’s Secure DNS Servers.
DNS Protection at the Network Gateway can also be deployed as an add-on service. This is useful to provide additional security for non-windows devices or for BYOD devices connecting through your corporate and guest wifi networks. Network DNS protection does not require a system agent on each protected device. Instead, protection is configured at the Network-Edge router so that ALL Internet DNS requests from ANY device on the network is funneled to Webroots secure DNS Servers.
Default DNS Protection Settings
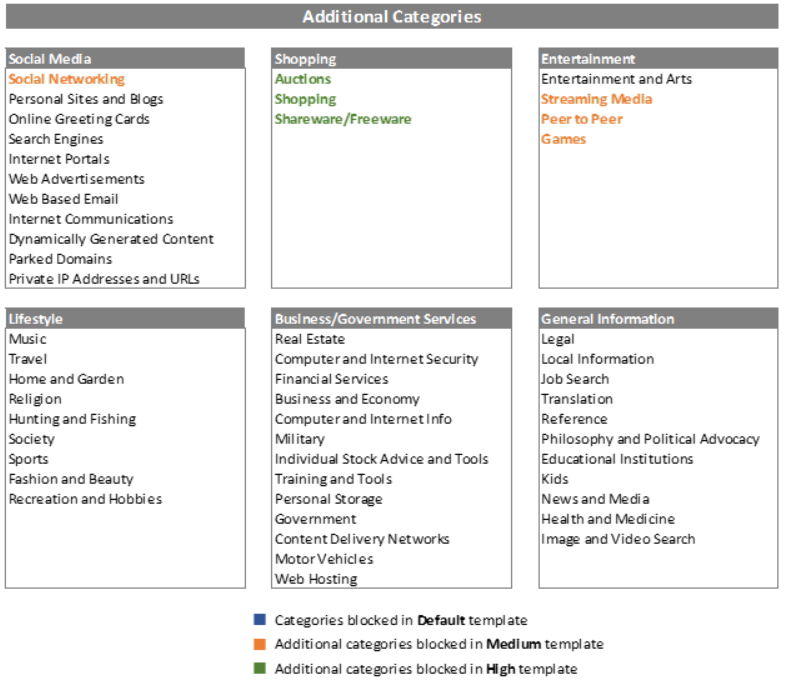
The Default TPx Webroot Secure DNS protection template blocks three categories of sites by default: “Security Risk”, “Human Resources”, and “Questionable and Legal”. Customers can also choose to place users into one of two Additional protection templates – Medium and High, to further enhance protection and policy enforcement. A group for “Uncategorized” sites exists, which will block anything new to the web that hasn’t been categorized by Webroot yet as harmful or otherwise. All users receive this protection by default. A detailed category list is provided below.
Reporting
TPx provides a monthly report that is automatically emailed to the customer. The report is organized into 6 sections as described below.
- Botnet Command & Control Blocked: Shows domains that have been blocked by DNS Protection and are categorized as Command and Control. This section highlights malicious activity that has been blocked by DNS Protection.
- Active Hosts: This section improves visibility of Internet usage and displays complete browsing history of devices within a site, including requested and block counts by device, username, domains, category, block reason, etc.
- Top Blocked Category: Includes an overview that shows blocked categories during the month. Security risk are grouped together for further analysis.
- Top Blocked Domain: Similar to the Top Blocked Categories, this section improves visibility of Internet usage by detailing the top 12 domains that were blocked by site.
- Top Requested Category: Provides insight into all domains being requested, organized by category
- Top Sites by Number of Requests: Designed for implementation of DNS Protection using the network setting, this section can be used to approximate traffic (Total number of DNS requests being made)