Importance of Cybersecurity in Business
Small Business Cybersecurity Topics
-
1Importance of Cybersecurity in Business
-
2Why Cybersecurity is Important for Small Business
-
3Common Cybersecurity Threats to Small Business
-
4What is a Good Small Business Cybersecurity Plan?
-
5Types of Cybersecurity Solutions for Small Business
-
6Should Small Businesses Manage Cybersecurity In-house or Outsource?
-
HomeBack to Learning Center

The importance of cybersecurity in business isn’t one thing but a series of actions to protect your business’ computing and communications infrastructure and applications from digital attacks by cybercriminals located anywhere in the world. It’s a never-ending battle against bad actors who intend to steal valuable data, disrupt operations and often hold your systems hostage for a profit.
It’s not just large enterprises that are under assault – companies of all sizes are at risk. Small and medium businesses (SMBs) are particularly vulnerable because cybercriminals view them as easy targets with limited defenses.
In today’s digital world, cybersecurity helps to mitigate potential security risks, including:
- Ransomware
- Identity theft
- Corporate espionage
- Malware
- Network intrusions
- Misuse of data
- System failure
- Data corruption
- Lost or stolen equipment
Protecting your digital assets has become a necessity. For your business, cybersecurity is critical to:
- Avoid downtime
- Protect company, customer and employee data
- Keep customers’ trust
- Maintain regulatory compliance
- Uphold your company’s reputation
It’s Not Only About Technology
There’s no single cure-all solution to the ongoing threats against your company’s network. There are many ways hackers can hurt your business and many ways to fight back.
Successful cybersecurity protection is a three-pronged approach that takes into consideration your people, processes and technologies. Let’s look at all three:
People
Your workforce will always be your weakest link, but also can be your most potent weapon. Ongoing training with an emphasis on ways of staying safe within the network can dramatically reduce your risk.
Processes
Defining and enforcing security practices are the basis for good cyber hygiene. But it also includes a strong incident response plan, which is well-rehearsed and documented to minimize damage and downtime.
Technology
Cybersecurity tools are evolving alongside cybersecurity threats and becoming more predictive. Keeping current is critical to staying safe.
It’s an Investment, Not a Cost
Whether it’s training your team, establishing policies and procedures, or implementing technology, cybersecurity requires an investment in time, talent and technology. For cost-conscious small and medium businesses (SMBs), the cost may be perceived as burdensome, but it’s small compared to what not having them will cost in the event of a breach.
Depending on how you define an SMB, statistics on breach costs vary greatly – from $200,000 to $4 million and everywhere in between. But the takeaway is the same – the cost of a data breach can be devastating.
It may help to think of cybersecurity like an insurance policy, which only seems like an unnecessary expenditure until you need it. And research shows that when it comes to cybersecurity, you’re likely to need it. The probability that your business will experience a breach is 29.6 percent, according to Ponemon Institute, which says this figure has been trending up over the 14-year span of its research (see chart below).
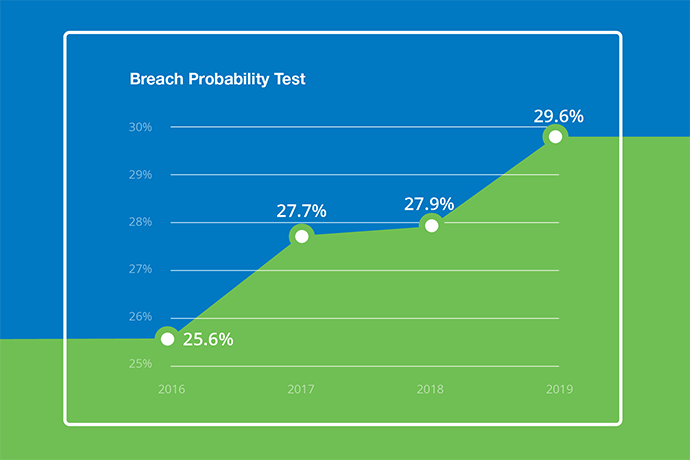
The good news is that effective cybersecurity also is available as a managed service (a.k.a. security as a service), which enables SMBs to source cybersecurity delivered by experts as an affordable monthly subscription. Managed security services mean you don’t have to invest upfront in security talent and technologies to get the protection you need. Plus, managed services subscriptions are often offset by not taking your IT personnel away from other critical operational or revenue-generating functions.
Need to strengthen cybersecurity for your business?
We can help! Get in touch with us below to speak to one of our experts.
"*" indicates required fields
